Cyber Security news is inundated with new ransomware attacks using current events to entice end users to open and click on an email that will encrypt data and demand ransom. Some however are far more invasive, such as the RYUK Ransomware, which is the final act in an attack, one that starts with the Emotet malware, followed by a deployment of Trickbot, and then the ransomware. The first parts of this attack allows the cyber criminals to determine, based on your data, what ransom should be set. It is also interesting to note the Emotet and Trickbot were primarily used to exfiltrate data, but as corporations struggle to recover from the ransomware, this may go unheeded until the information is available through nefarious channels, and of course then an organization becomes a headline.
While not by definition an Advanced Persistent Threat, which is defined as “a prolonged and targeted cyberattack in which an intruder gains access to a network and remains undetected for an extended period of time. The intention of an APT attack is usually to monitor network activity and steal data rather than to cause damage to the network or organization.“ Both of these types of attacks are stealthy, and can avoid detection, unless using a system that that monitors and analyzes the activity on individual systems.
Snare Agents are designed to send event log data in real time and can be configured to monitor specific Windows Registry keys and system folders that are common malware load points. In each of the various versions of windows, there are specific locations within the file systems and registry that are used to load applications and related files. While these are used by legitimate programs, they are also commonly used as attached vectors for malware. Malware needs to be installed persistently, so that it remains active in the event of reboot, and most persistent techniques on the windows platform involve the use of the Windows Registry.
Certain registry keys may contain values used to load applications, and in this instance malware, when Windows is started. This is extremely difficult to mitigate this with traditional preventative tools, however using the Snare Agent to monitor the registry can assist in the detection of this threat.
There are specific run keys that are created by default with the Windows Systems:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
In addition, other Registry keys can be used for persistence:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ Explorer\User Shell Folders
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ Explorer\Shell Folders
With the Snare Agent it is incredibly easy to create a rule to monitor:
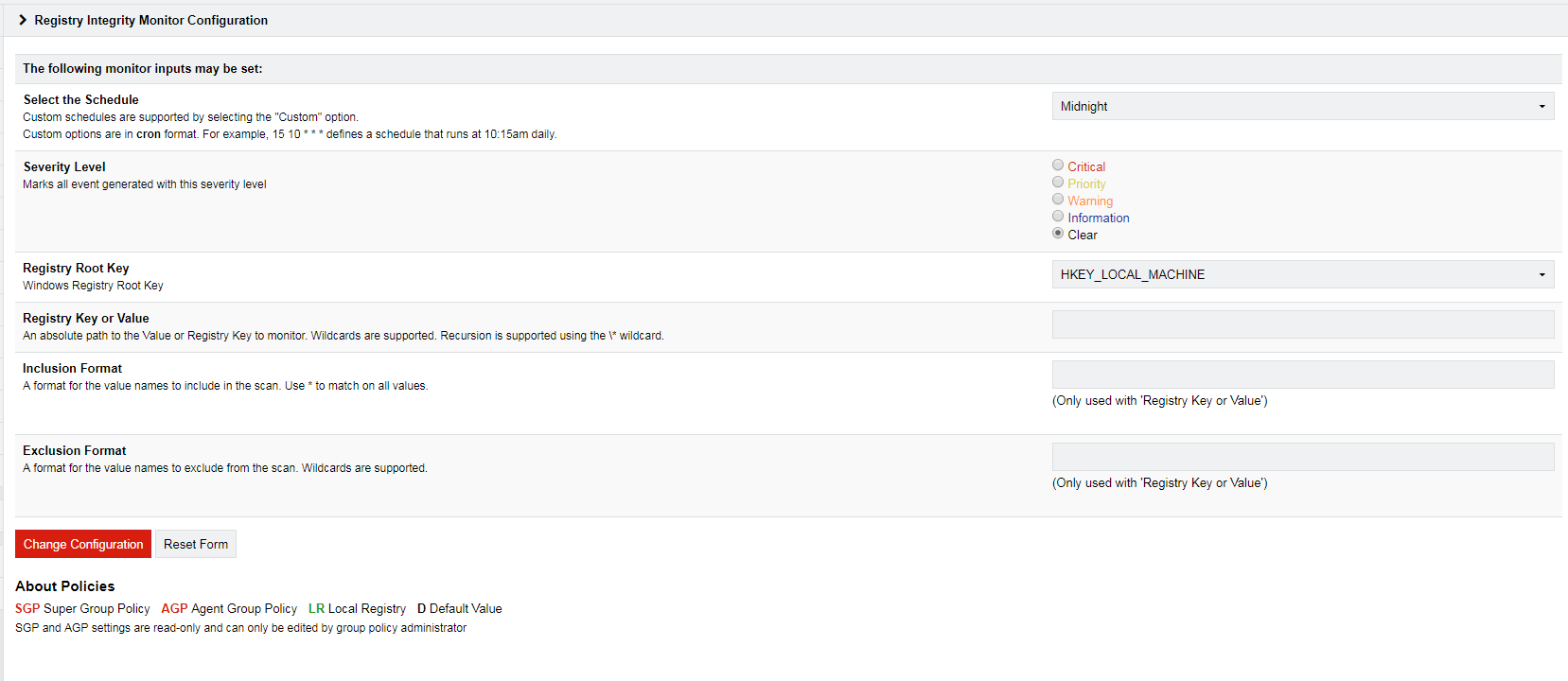
Chose to configure the Registry Integrity Monitoring
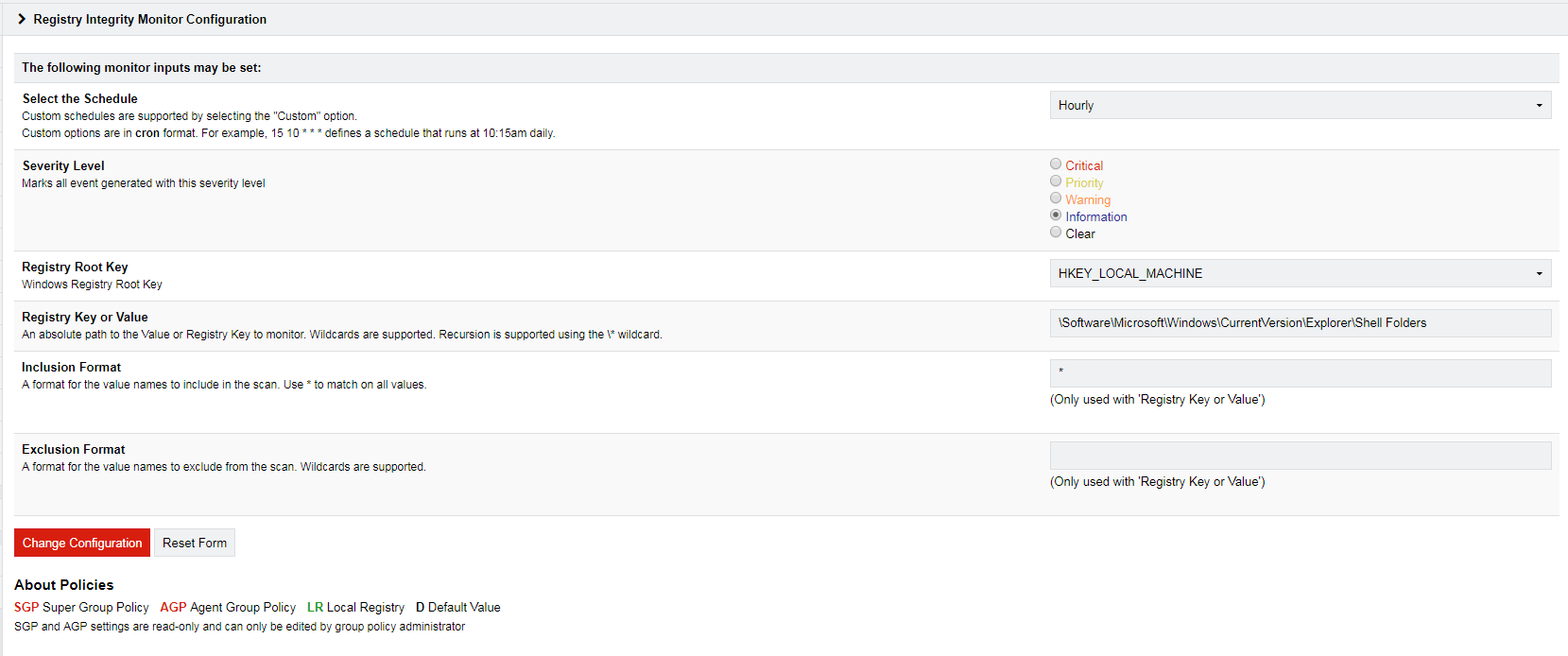
Set the registry keys you wish to monitor, apply and restart.
It will capture the baseline of the current registry key, and then monitor any changes to that key, and send to your SIEM or Snare Central, providing you with the digital footprint of malicious activity.




