Snare XDR and Sysmon
Threat detection software has evolved significantly in recent years. Malware detection and prevention software began incorporating endpoint detection and response (EDR) in a change of tactics in response to more comprehensive, dangerous, and self-masking malware variants. The market has adopted a few different flavours of Detect/Response mechanisms – EDR, Network Detection and Response (NDR), Threat Detection and Response (TDR), and now the industry has settled more on Extended Detection and Response (XDR).
The terms have meant different things to different customers and vendors, but the overall goal is to detect and react to threats and unauthorised user activity across networks, servers and endpoints, clouds, and applications. XDR applies analytics and automation to detect, analyse, and hunt for threats in order to remediate or respond to identified threats.
By collecting forensic and log data from a diverse range of system components, correlated data can be scanned to identify patterns across event sources and provide context to a threat or attack chain. Events and activities that would not have been detected or addressed prior to XDR tools and concepts being implemented will be more obvious, allowing security teams to focus on, respond to, and mitigate/eliminate identified threat. This has the benefit of reducing further impact, and dropping the severity, scope, and longevity of the attack.
How Snare helps with XDR
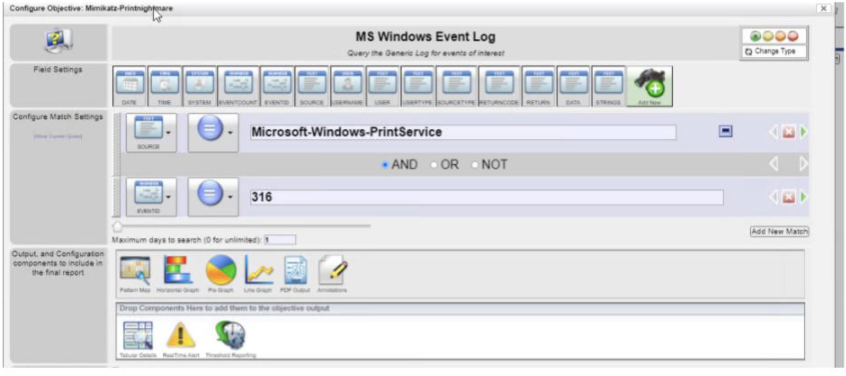
The Snare suite has a comprehensive capability to collect log data from almost any source. Snare agents run on most common platforms such as Windows, Linux variations, MacOS, Solaris, Microsoft SQL Server, and can collect relevant forensic log activity from a wide range of systems and applications. The Snare agents collect and send log data to a Snare Central server and can send or reflect data to a range of other SIEM and analytics tools. The collected logs provide visibility into a range of security-sensitive activities, including:
- Administrative Activity – What actions were undertaken by administrative users? Did they add/remove users, change permissions, change system policies, run privileged commands, etc.?
- Login/Logoff Activity – Who logged on, was it within business hours or out of hours, what systems were impacted? Was it local or remote via a VPN or remote connection to the host? What was the source? Was there lateral user movement between systems? Are users trying to gain privileged access to systems? Are there indications of brute force logins occurring on the network to attempt to guess a password?
- Command Activity – What applications or shell commands were run, were any executed at a higher privilege level? Where were these commands run, on what systems?
- Data Access – What data was accessed, by who? What did they read, change, or delete? Was data copied or exfiltrated to other systems or out over the internet? Was a file or payload or backdoor loaded by malicious actors for later use?
There are various capabilities that help facilitate the analysis of these activities:
- Collect logs from as many sources as possible – all servers, desktops, network devices, everything that can send a syslog. All devices should have some form of logging or monitoring in place.
- Use FIM, FAM, RIM and RAM to track and monitor all key files and system configuration. Know who and when files were changing and what tools they used.
- Use Database Activity Monitoring (DAM) to track key activity on SQL databases. Know if admin accounts are being abused and validate that key data has not been tampered with.
- Having evidence to show if the attack vectors came in via email, USB, a web link download, a software update are all important to knowing how they got in.
To take a deeper dive into how Snare can help with XDR, download our technical white paper.