BLOG
Every year, organisations face a familiar but escalating challenge: volume. Volume of attacks. Volume of activity. Volume of logs. Volume of costs.
And that volume is growing faster than most security teams, SIEM platforms, or budgets can keep up with.
Snare customers around the world report the same trend: their data isn’t just growing — it’s exploding. The modern cyber landscape is now defined by scale, speed, and complexity that legacy log management approaches simply cannot handle.
Let’s break down the four dimensions of the cyber volume crisis — and how security teams can take back control.
1. The Volume of Cyber Activity Is Skyrocketing
Every endpoint, workload, system, user, and device produces a trail of digital activity. In the average mid-to-large enterprise, this quickly becomes unmanageable:
- Tens of thousands of daily authentication events
- Millions of process executions, system calls, and file interactions
- Continuous API, cloud, and container activity
- Expanding hybrid and multi-cloud footprints
- More remote workers, more unmanaged devices, more shadow IT
More activity means more noise. More noise means more complexity. And more complexity means more risk.
Without the right log collection and filtering strategy, teams are forced to choose between losing visibility or drowning in unnecessary events. Snare eliminates that trade-off — capturing forensic-grade detail while keeping ingestion lean and optimised.
2. The Volume of Cyber Attacks Is Accelerating — Whether They Succeed or Not
Attackers are scaling too.
Today’s threat actors launch waves of automated attempts, probing every exposed service, credential, and misconfiguration. Many fail, but every attempt matters when you’re responsible for detection and reporting.
Across our customer base and the wider cybersecurity industry, this trend is clear:
- Billions of automated attack attempts occur globally each day
- Organisations face persistent credential stuffing and brute-force attempts
- High-speed scanning tools hit networks 24/7
- Ransomware operators now run like enterprise businesses
- AI-assisted attacks increase speed, sophistication, and reach
This means defenders must log more, analyse more, and retain more — even when attacks are blocked.
Snare’s ultra-efficient event collection and compression ensure teams capture what they need to prove what happened — or what didn’t.
3. The Volume of Logs Required for Compliance & Forensics Keeps Growing
Most regulatory frameworks demand detailed and long-term log retention:
- PCI DSS: 1 year
- ISO 27001: months to years depending on policy
- HIPAA: 6+ years
- NIST SP 800-53: extensive audit logging requirements
- Australian Government ISM & PSPF: strict retention and visibility requirements
This means you can’t simply delete logs to save costs — not without risking fines, gaps in evidence, or failed audits.
At the same time:
- SIEM ingestion costs are increasing
- Retention tiers are becoming more expensive
- Logs now include enriched metadata, resulting in larger events
- Cloud systems generate high-volume logs constantly
- Forensic-level detail is mandatory to reconstruct incidents
Snare solves this by combining granular filtering, optimised compression, long-term cold storage, and features like Log Replay — allowing you to store logs affordably and replay them back into Splunk, Sentinel, or other tools only when needed.
You retain everything. You pay for only what matters.
4. The Volume of Costs Is Becoming Unsustainable
As data volumes rise, so do the bills:
- SIEM ingestion
- Cloud storage
- License tiers
- Indexing and query usage
- Compliance-mandated retention
- IR consulting during investigations
Many organisations report that log-related costs now consume the majority of their security budget.
Snare flips the model:
- Up to 90% SIEM cost reduction with filtering & offload
- Massive storage savings with highly compressed cold storage
- Predictable cost control with tiered subscription models
- Pay for coverage, not for noise
- Replay-only-when-needed for investigations, audits, and threat hunting
This is how modern security teams regain financial control without sacrificing visibility.
Snare: Built for the Volume Era of Cybersecurity
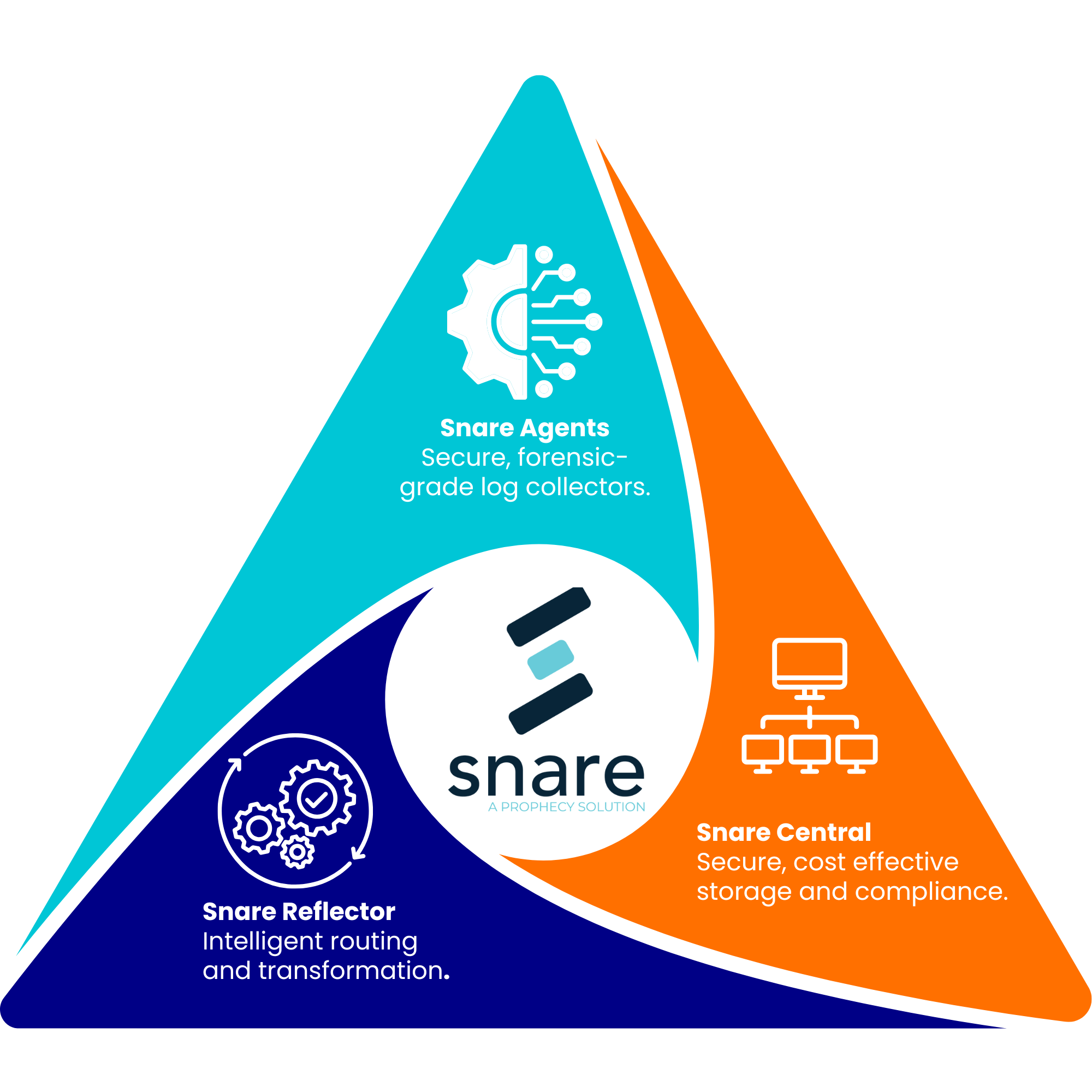
Snare is purpose-built for environments where scale, speed, and forensic accuracy matter. Across the Snare Suite — Snare Agents, Snare Central, Snare Reflector — customers gain:
- High-fidelity forensic-grade logging
- High-throughput, low-latency collection
- Smart filtering at the source
- Optimised compression for long-term retention
- Flexible storage options for cost control
- Native integrations to Splunk HEC, Sentinel, and modern SIEMs
- Log Replay for retrospective investigations without hot storage costs
In a world where “more” is the new normal — more attacks, more systems, more logs — Snare gives security teams a way to keep up without breaking their SIEM or their budget.